Our Trust Center
Reflects our commitment to providing a secure environment and adopting effective security standards.
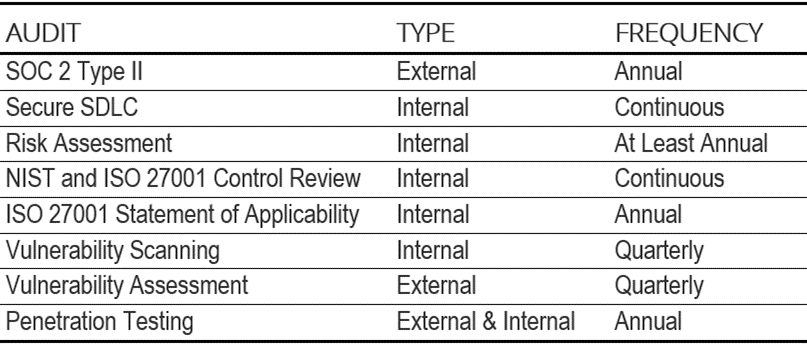
We recognize the importance of maintaining the confidentiality, integrity, and availability of our clients’ data and the protection of their valuable business assets and applications. Our Trust Center reflects our commitment to providing a secure environment and adopting effective security standards that exceed industry best practices in the areas of information security and compliance.
With a variety of reliable security technologies, as well as a unique combination of trained personnel, mature business processes, and regular third-party audits measured against several international and U.S. standards, we deliver a high level of security and confidence that is unmatched in the industry.
Our Trust Center describes each layer of this assurance approach to provide an overview of the compliance, data protection, and cybersecurity that we provide.